《新剑与魔法》4月15日16点登陆异常修复公告
Policy-Based Access Control Approach to Staff Activities of a Business Process Download PDFInfo
- Publication number
- US20080263060A1 US20080263060A1 US11/738,794 US73879407A US2008263060A1 US 20080263060 A1 US20080263060 A1 US 20080263060A1 US 73879407 A US73879407 A US 73879407A US 2008263060 A1 US2008263060 A1 US 2008263060A1
- Authority
- US
- United States
- Prior art keywords
- access control
- staff activity
- control system
- staff
- user
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
- 238000000034 method Methods 0.000 title claims abstract description 165
- 230000008569 process Effects 0.000 title claims abstract description 148
- 230000000694 effects Effects 0.000 title claims abstract description 115
- 238000012545 processing Methods 0.000 claims abstract description 40
- 238000004590 computer program Methods 0.000 claims abstract description 13
- 238000011161 development Methods 0.000 claims abstract description 9
- 230000000977 initiatory effect Effects 0.000 claims abstract description 5
- 238000013475 authorization Methods 0.000 claims description 9
- 230000009471 action Effects 0.000 claims description 6
- 238000004891 communication Methods 0.000 claims description 6
- 238000011165 process development Methods 0.000 claims description 6
- 230000027455 binding Effects 0.000 abstract description 21
- 238000009739 binding Methods 0.000 abstract description 21
- 230000015654 memory Effects 0.000 description 22
- 230000008520 organization Effects 0.000 description 8
- 230000008859 change Effects 0.000 description 5
- 238000010586 diagram Methods 0.000 description 5
- 238000005516 engineering process Methods 0.000 description 4
- 238000007726 management method Methods 0.000 description 4
- 230000003287 optical effect Effects 0.000 description 4
- 230000003068 static effect Effects 0.000 description 4
- 238000013070 change management Methods 0.000 description 3
- 238000013507 mapping Methods 0.000 description 3
- 238000012986 modification Methods 0.000 description 3
- 230000004048 modification Effects 0.000 description 3
- 230000008901 benefit Effects 0.000 description 2
- 239000004744 fabric Substances 0.000 description 2
- 230000006870 function Effects 0.000 description 2
- 230000002093 peripheral effect Effects 0.000 description 2
- 239000004065 semiconductor Substances 0.000 description 2
- 230000005540 biological transmission Effects 0.000 description 1
- 239000000835 fiber Substances 0.000 description 1
- 230000008676 import Effects 0.000 description 1
- 230000003993 interaction Effects 0.000 description 1
- 230000007246 mechanism Effects 0.000 description 1
- 239000007787 solid Substances 0.000 description 1
- 238000012546 transfer Methods 0.000 description 1
Images
Classifications
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY?PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q10/00—Administration; Management
- G06Q10/06—Resources, workflows, human or project management; Enterprise or organisation planning; Enterprise or organisation modelling
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/30—Information retrieval; Database structures therefor; File system structures therefor of unstructured textual data
- G06F16/36—Creation of semantic tools, e.g. ontology or thesauri
- G06F16/367—Ontology
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F9/00—Arrangements for program control, e.g. control units
- G06F9/06—Arrangements for program control, e.g. control units using stored programs, i.e. using an internal store of processing equipment to receive or retain programs
- G06F9/44—Arrangements for executing specific programs
- G06F9/448—Execution paradigms, e.g. implementations of programming paradigms
- G06F9/4488—Object-oriented
- G06F9/4492—Inheritance
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F9/00—Arrangements for program control, e.g. control units
- G06F9/06—Arrangements for program control, e.g. control units using stored programs, i.e. using an internal store of processing equipment to receive or retain programs
- G06F9/46—Multiprogramming arrangements
- G06F9/50—Allocation of resources, e.g. of the central processing unit [CPU]
- G06F9/5005—Allocation of resources, e.g. of the central processing unit [CPU] to service a request
- G06F9/5027—Allocation of resources, e.g. of the central processing unit [CPU] to service a request the resource being a machine, e.g. CPUs, Servers, Terminals
- G06F9/5055—Allocation of resources, e.g. of the central processing unit [CPU] to service a request the resource being a machine, e.g. CPUs, Servers, Terminals considering software capabilities, i.e. software resources associated or available to the machine
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY?PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q10/00—Administration; Management
- G06Q10/06—Resources, workflows, human or project management; Enterprise or organisation planning; Enterprise or organisation modelling
- G06Q10/063—Operations research, analysis or management
- G06Q10/0631—Resource planning, allocation, distributing or scheduling for enterprises or organisations
- G06Q10/06311—Scheduling, planning or task assignment for a person or group
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY?PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q10/00—Administration; Management
- G06Q10/06—Resources, workflows, human or project management; Enterprise or organisation planning; Enterprise or organisation modelling
- G06Q10/063—Operations research, analysis or management
- G06Q10/0631—Resource planning, allocation, distributing or scheduling for enterprises or organisations
- G06Q10/06311—Scheduling, planning or task assignment for a person or group
- G06Q10/063118—Staff planning in a project environment
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY?PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q10/00—Administration; Management
- G06Q10/06—Resources, workflows, human or project management; Enterprise or organisation planning; Enterprise or organisation modelling
- G06Q10/067—Enterprise or organisation modelling
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06Q—INFORMATION AND COMMUNICATION TECHNOLOGY [ICT] SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY PURPOSES; SYSTEMS OR METHODS SPECIALLY ADAPTED FOR ADMINISTRATIVE, COMMERCIAL, FINANCIAL, MANAGERIAL OR SUPERVISORY?PURPOSES, NOT OTHERWISE PROVIDED FOR
- G06Q10/00—Administration; Management
- G06Q10/10—Office automation; Time management
- G06Q10/103—Workflow collaboration or project management
Definitions
- the present invention relates generally to an improved data processing system, and in particular, to dynamically binding business process activities to human entities at deployment time.
- Business processes define a set of coordinated tasks and activities that lead to accomplishing specific goals of an organization.
- Business processes may be implemented in a proprietary software language or may be implemented using an industry standard language, such as the Business Process Execution Language (BPEL).
- BPEL Business Process Execution Language
- a business process may include activities which comprise automated tasks, which are performed by computers or other machines, as well as manual activities, which require some form of human intervention.
- activities requiring human intervention is a process in which a request for a change is received, and a human entity must assess the impact and give approval of the requested change prior to the change being implemented. Activities requiring human intervention are often called “staff activities”.
- a particular administrator may be responsible for maintaining a particular subnet of devices with a range of IP addresses between X.Y.Z.0 and X.Y.Z.255.
- the administrator may log into the management system and attempt to manage a device at address X.Y.Z.5.
- the network management system uses the security policy to determine whether to allow the administrator to perform the management function on that particular device. The process of deciding which users are allowed to perform specific activities in a business process is called “staff resolution”.
- the illustrative embodiments provide a computer implemented method, data processing system, and computer program product for dynamically binding business process activities to human entities at deployment time.
- Identification information about a staff activity in a business process is received from a process server at an access control system external to the process server. Responsive to initiation of the business process, the staff activity is resolved at the access control system at runtime by assigning the staff activity to a user based on an access policy of the access control system to form a staff activity assignment. The staff activity assignment is communicated from the access control system to the process server.
- the process in the illustrative embodiments allows the development of the business process to be entirely decoupled from staff activity resolution at runtime.
- FIG. 1 depicts a pictorial representation of a distributed data processing system in which the illustrative embodiments may be implemented
- FIG. 2 is a block diagram of a data processing system in which the illustrative embodiments may be implemented
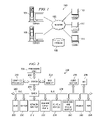
- FIG. 3 is a block diagram of exemplary components for implementing the policy-based access control of business process activities in accordance with the illustrative embodiments.
- FIG. 4 is a flowchart of a process for dynamically binding business process activities to human entities in accordance with the illustrative embodiments.
- FIGS. 1-2 exemplary diagrams of data processing environments are provided in which illustrative embodiments may be implemented. It should be appreciated that FIGS. 1-2 are only exemplary and are not intended to assert or imply any limitation with regard to the environments in which different embodiments may be implemented. Many modifications to the depicted environments may be made.
- FIG. 1 depicts a pictorial representation of a network of data processing systems in which illustrative embodiments may be implemented.
- Network data processing system 100 is a network of computers in which the illustrative embodiments may be implemented.
- Network data processing system 100 contains network 102 , which is the medium used to provide communications links between various devices and computers connected together within network data processing system 100 .
- Network 102 may include connections, such as wire, wireless communication links, or fiber optic cables.
- network data processing system 100 is the Internet with network 102 representing a worldwide collection of networks and gateways that use the Transmission Control Protocol/Internet Protocol (TCP/IP) suite of protocols to communicate with one another.
- TCP/IP Transmission Control Protocol/Internet Protocol
- At the heart of the Internet is a backbone of high-speed data communication lines between major nodes or host computers, consisting of thousands of commercial, governmental, educational and other computer systems that route data and messages.
- network data processing system 100 also may be implemented as a number of different types of networks, such as for example, an intranet, a local area network (LAN), or a wide area network (WAN).
- FIG. 1 is intended as an example, and not as an architectural limitation for the different illustrative embodiments.
- Data processing system 200 is an example of a computer, such as server 104 or client 110 in FIG. 1 , in which computer usable program code or instructions implementing the processes may be located for the illustrative embodiments.
- data processing system 200 employs a hub architecture including a north bridge and memory controller hub (NB/MCH) 202 and a south bridge and input/output (I/O) controller hub (SB/ICH) 204 .
- NB/MCH north bridge and memory controller hub
- SB/ICH south bridge and input/output controller hub
- Processing unit 206 , main memory 208 , and graphics processor 210 are coupled to north bridge and memory controller hub 202 .
- Processing unit 206 may contain one or more processors and even may be implemented using one or more heterogeneous processor systems.
- Graphics processor 210 may be coupled to the NB/MCH through an accelerated graphics port (AGP), for example.
- AGP accelerated graphics port
- local area network (LAN) adapter 212 is coupled to south bridge and I/O controller hub 204 and audio adapter 216 , keyboard and mouse adapter 220 , modem 222 , read only memory (ROM) 224 , universal serial bus (USB) and other ports 232 , and PCI/PCIe devices 234 are coupled to south bridge and I/O controller hub 204 through bus 238 , and hard disk drive (HDD) 226 and CD-ROM 230 are coupled to south bridge and I/O controller hub 204 through bus 240 .
- PCI/PCIe devices may include, for example, Ethernet adapters, add-in cards, and PC cards for notebook computers. PCI uses a card bus controller, while PCIe does not.
- ROM 224 may be, for example, a flash binary input/output system (BIOS).
- Hard disk drive 226 and CD-ROM 230 may use, for example, an integrated drive electronics (IDE) or serial advanced technology attachment (SATA) interface.
- IDE integrated drive electronics
- SATA serial advanced technology attachment
- a super I/O (SIO) device 236 may be coupled to south bridge and I/O controller hub 204 .
- An operating system runs on processing unit 206 and coordinates and provides control of various components within data processing system 200 in FIG. 2 .
- the operating system may be a commercially available operating system such as Microsoft? Windows? XP (Microsoft and Windows are trademarks of Microsoft Corporation in the United States, other countries, or both).
- An object oriented programming system such as the JavaTM programming system, may run in conjunction with the operating system and provides calls to the operating system from JavaTM programs or applications executing on data processing system 200 .
- JavaTM and all JavaTTM-based trademarks are trademarks of Sun Microsystems, Inc. in the United States, other countries, or both.
- Instructions for the operating system, the object-oriented programming system, and applications or programs are located on storage devices, such as hard disk drive 226 , and may be loaded into main memory 208 for execution by processing unit 206 .
- the processes of the illustrative embodiments may be performed by processing unit 206 using computer implemented instructions, which may be located in a memory such as, for example, main memory 208 , read only memory 224 , or in one or more peripheral devices.
- FIGS. 1-2 may vary depending on the implementation.
- Other internal hardware or peripheral devices such as flash memory, equivalent non-volatile memory, or optical disk drives and the like, may be used in addition to or in place of the hardware depicted in FIGS. 1-2 .
- the processes of the illustrative embodiments may be applied to a multiprocessor data processing system.
- data processing system 200 may be a personal digital assistant (PDA), which is generally configured with flash memory to provide non-volatile memory for storing operating system files and/or user-generated data.
- PDA personal digital assistant
- a bus system may be comprised of one or more buses, such as a system bus, an I/O bus and a PCI bus. Of course the bus system may be implemented using any type of communications fabric or architecture that provides for a transfer of data between different components or devices attached to the fabric or architecture.
- a communications unit may include one or more devices used to transmit and receive data, such as a modem or a network adapter.
- a memory may be, for example, main memory 208 or a cache such as found in north bridge and memory controller hub 202 .
- a processing unit may include one or more processors or CPUs.
- processors or CPUs may include one or more processors or CPUs.
- FIGS. 1-2 and above-described examples are not meant to imply architectural limitations.
- data processing system 200 also may be a tablet computer, laptop computer, or telephone device in addition to taking the form of a PDA.
- business processes are computer processes which are often customized to a particular company's needs and typically involve some amount of human interaction. Since most organizations classify their personnel into different organizational roles based on the tasks performed by each individual, the actions of any particular individual may be restricted to those operations that are appropriate for the individual's role in the organization based on policy rules.
- the process of binding a task to an individual or organizational role (“staff resolution”) comprises deciding which user in the organization is allowed to perform the activity in a business process.
- the illustrative embodiments provide a dynamic method and system for binding a business process activity to a corresponding human entity or organizational role.
- the illustrative embodiments decouple the policy-based authorization from the process engine and externalize this authorization in a policy-based access control system.
- binding is implemented at deployment time through the policy-based access control system.
- the dynamic process in the illustrative embodiments does not need to rely on definitions created at development time to implement the binding process, and thus the process avoids the static nature of existing staff resolution techniques.
- implementing the binding process at deployment time in the access control system shields a user from having to re-build and re-deploy a business process when a change occurs in the underlying definitions which enable staff resolution.
- the dynamic staff resolution process described in the illustrative embodiments provides several advantages over existing staff resolution techniques. For instance, with the illustrative embodiments, the binding of human entities to staff activities of a process is completely dynamic and is process-independent. Existing staff resolution techniques implement this binding as part of the process logic. Thus, a business process developer using the illustrative embodiments may focus solely on the business process logic at development time, rather than having to be concerned over binding of staff activities to human entities.
- human intervention during business process activities may be subject to various rules. For instance, a particular approval process may require the approval of an entire set of persons exercising a particular role or a subset thereof. Similarly, another policy may render the tasks to an automatic approval based on the satisfaction of pre-set conditions.
- the binding in the illustrative embodiments is delegated to an access control system, roles, users and deciding rules may be updated at deployment time to accommodate the needs of the organization.
- the staff service component in products such as Websphere Process Choreographer becomes a very light-weight component of the process engine, as the staff service component simply acts as an interface to the underlying access control system.
- FIG. 3 is a block diagram of exemplary components for implementing the policy-based access control of business process activities in accordance with the illustrative embodiments.
- FIG. 3 illustrates how the binding of human entities to business process activities is implemented within an access control system.
- Data processing system 300 in this illustrative example comprises business process engine 302 , access control interface 304 , and access control system 306 .
- Business process engine 302 is a process server, which may be implemented as server 104 or 106 in FIG. 1 .
- Business process engine 302 contains the runtime components necessary to execute a business process, and interprets the business processes defined by a business process developer in order to execute and manage business transactions.
- Business process engine 302 oversees the business transactions in the data processing system by reminding an individual or group participant of their assigned staff activities, such as via a calendar or email program.
- Business process engine 302 also may act as a client device to access control system 306 .
- Access control interface 304 allows business process engine 302 to interface with external systems.
- a JavaTM Authorization Contract for Container (JACC) interface is used as the access control interface 304 , although other appropriate interfaces may also be used.
- JACC provides the ability to delegate access decisions to an external provider, such as access control system 306 .
- Business process engine 302 is interfaced via JACC to access control system 306 .
- Access control system 306 is an authorization provider external to business process engine 302 which receives information about a user security context and determines whether any activities are assigned to the user. Access control system 306 may be located on any server 104 or 106 in FIG. 1 . Access control system 306 protects resources (business process activities) in the system by making them available to users who are identified as assigned to those resources. Access control system 306 may include a user registry, such as a corporate LDAP server or a database, comprising user and group/role information. Resources may be defined and mapped to particular users and roles within the organization to constrain resource access based on these mappings. This mapping may be to one or more individual users by name, to one or more defined groups of users, or any combination of these. These mappings may be stored as role-based access control lists (ACLs) within access control system 306 .
- An example of an access control system is Tivoli? Access Manager, a product of International Business Machines Corporation.
- a process development tool outputs only identification information of the staff activities 310 contained in a business process.
- identification information of each staff activity 310 may be output in a tuple, such as:
- Business process engine 302 then exports the identification information of a staff activity 310 in tuple form, and imported to an authorization policy engine in access control system 306 .
- the authorization policy engine in access control system 306 comprises policy information required to determine the binding of each staff activity to a corresponding human entity or an organizational role, or to a rule based policy statement when access control system 306 supports such rules.
- Access control system 306 then stores the tuple in access policy store 312 . It should be noted that storing staff activity information within access control system 306 is a departure from existing staff resolution mechanisms which persist this staff activity information in their own control structures, rather than in a control system external to access control system 306 .
- Access policy store 312 also comprises role-based access control lists (ACLs), which access control system 306 uses to form the bindings between the staff activities and the human entities or organizational roles based on the information in the tuple.
- ACLs role-based access control lists
- business process engine 302 may invoke access control system 306 by passing the user security context (e.g. an authenticated identity and its group/role information) to access control system 306 .
- user security context e.g. an authenticated identity and its group/role information
- Access control system 306 queries the access control lists (ACLs) in access policy store 312 against the user information and returns ? Process Name, Activity Name> of each activity that is awaiting the user's intervention.
- Business process engine 302 provides this user information to access control system 306 and allows access control system 306 to make an access decision (i.e., a determination whether the user has any pending staff activities assigned).
- Access control system 306 provides the pending staff activity information to business process engine 302 , which in turn provides the activity information to the user.
- Access control system 306 may also determine whether or not access to a resource may be given to an entity by first determining whether the entity has access to the process activity template. For example, a change requester may instantiate a change management process only if the requester is allowed access to the underlying change management process template.
- a process template is a generic process definition that has not yet been customized to a particular environment, such as a change management process template in which staff activities have not yet been defined.
- FIG. 4 is a flowchart of a process for dynamically binding business process activities to human entities in accordance with the illustrative embodiments.
- the process described in FIG. 4 may be implemented in a data processing system, such as data processing system 300 in FIG. 3 .
- the process begins at development time, where a process development tool used to define a process outputs information about all of the tool's staff activities (step 402 ).
- This information may comprise identification information about the staff activities in tuple form, which includes an identifier of a business process, an identifier of a particular staff activity in the process, and the business objects which will be affected by the actions of the staff activity.
- the process server then exports the identification information containing information about the staff activity in tuple form to an authorization policy engine in an external access control system (step 404 ).
- the access control system comprises policy information required to determine the binding of each business activity to a corresponding human entity or an organizational role.
- the external access control system then imports and stores the identification information in an access policy store within the access control system (step 406 ).
- the business process instructs the external access control system to resolve the staff activities in the business process which have no dependency on other staff activities (step 408 ).
- resolution means assigning staff activities to the entitled human entities based on the access policy of the access control system.
- the resolved staff activities are communicated back from the access control system to the process server (step 410 ).
- the process server When a user authenticates (logs on) to the process server and checks if the user has a pending staff activity, the process server provides the user with those staff activities which were assigned to the user by the access control system based on the access policy (step 412 ). For example, the process server may provide the business process name and the business activity name to the user which are pending the user's intervention. The user may then perform the business activities dynamically assigned to the user by the access control system (step 414 ).
- step 416 A determination is then made as to whether there are any other staff activities in the business process which should be resolved (step 416 ). If there are more staff activities to be resolved (‘yes’ output of step 416 ), the process loops back to step 408 . If there are no more staff activities to be resolved (‘no’ output of step 416 ), the process terminates thereafter.
- the invention can take the form of an entirely hardware embodiment, an entirely software embodiment or an embodiment containing both hardware and software elements.
- the invention is implemented in software, which includes but is not limited to firmware, resident software, microcode, etc.
- the invention can take the form of a computer program product accessible from a computer-usable or computer-readable medium providing program code for use by or in connection with a computer or any instruction execution system.
- a computer-usable or computer readable medium can be any tangible apparatus that can contain, store, communicate, propagate, or transport the program for use by or in connection with the instruction execution system, apparatus, or device.
- the medium can be an electronic, magnetic, optical, electromagnetic, infrared, or semiconductor system (or apparatus or device) or a propagation medium.
- Examples of a computer-readable medium include a semiconductor or solid state memory, magnetic tape, a removable computer diskette, a random access memory (RAM), a read-only memory (ROM), a rigid magnetic disk and an optical disk.
- Current examples of optical disks include compact disk—read only memory (CD-ROM), compact disk—read/write (CD-R/W) and DVD.
- a data processing system suitable for storing and/or executing program code will include at least one processor coupled directly or indirectly to memory elements through a system bus.
- the memory elements can include local memory employed during actual execution of the program code, bulk storage, and cache memories which provide temporary storage of at least some program code in order to reduce the number of times code must be retrieved from bulk storage during execution.
- I/O devices including but not limited to keyboards, displays, pointing devices, etc.
- I/O controllers can be coupled to the system either directly or through intervening I/O controllers.
- Network adapters may also be coupled to the system to enable the data processing system to become coupled to other data processing systems or remote printers or storage devices through intervening private or public networks.
- Modems, cable modem and Ethernet cards are just a few of the currently available types of network adapters.
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- Software Systems (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Business, Economics & Management (AREA)
- General Engineering & Computer Science (AREA)
- Economics (AREA)
- Entrepreneurship & Innovation (AREA)
- Human Resources & Organizations (AREA)
- Strategic Management (AREA)
- Game Theory and Decision Science (AREA)
- Development Economics (AREA)
- Quality & Reliability (AREA)
- General Business, Economics & Management (AREA)
- Operations Research (AREA)
- Marketing (AREA)
- Educational Administration (AREA)
- Tourism & Hospitality (AREA)
- Life Sciences & Earth Sciences (AREA)
- Animal Behavior & Ethology (AREA)
- Computational Linguistics (AREA)
- Data Mining & Analysis (AREA)
- Databases & Information Systems (AREA)
- Management, Administration, Business Operations System, And Electronic Commerce (AREA)
Abstract
Description
- 百度 由国家工商总局广告监督管理司、消费者报社和中国消费网联合举办的首届典型违法广告形式漫画大奖赛近日圆满落幕。
1. Field of the Invention
- The present invention relates generally to an improved data processing system, and in particular, to dynamically binding business process activities to human entities at deployment time.
- 2. Description of the Related Art
- Business processes define a set of coordinated tasks and activities that lead to accomplishing specific goals of an organization. Business processes may be implemented in a proprietary software language or may be implemented using an industry standard language, such as the Business Process Execution Language (BPEL). A business process may include activities which comprise automated tasks, which are performed by computers or other machines, as well as manual activities, which require some form of human intervention. One example of an activity requiring human intervention is a process in which a request for a change is received, and a human entity must assess the impact and give approval of the requested change prior to the change being implemented. Activities requiring human intervention are often called “staff activities”.
- Most organizations classify their personnel into different roles based on the activities performed by each user. For example, a service provider may assign different individuals to manage different customers, different regions, and different groups of devices. In addition, users with different skill sets may assume different duties within the organization. Policy rules may be used to restrict the actions of any particular user to those operations that are appropriate for the user's role. For instance, in a typical network management system of possibly thousands of devices, the system may contain a security policy for the network administrator, for example, by assigning a specific class of privileges to the administrator based on the administrator's group. Within a runtime environment, the administrator can attempt to perform certain administrative functions that are not allowed to be performed by the average user. For example, a particular administrator may be responsible for maintaining a particular subnet of devices with a range of IP addresses between X.Y.Z.0 and X.Y.Z.255. At some point, the administrator may log into the management system and attempt to manage a device at address X.Y.Z.5. The network management system uses the security policy to determine whether to allow the administrator to perform the management function on that particular device. The process of deciding which users are allowed to perform specific activities in a business process is called “staff resolution”.
- Current technologies include specialized components which allow for staff resolution of business activities to the respective human entities in the organization's personnel. An example of a product capable of staff resolution is Websphere? Application Server Enterprise Process Choreographer, also called Websphere Process Server, which is a product of International Business Machines Corporation. The staff service component in the Process Choreographer and in other current technologies is provided by and supported by the process engine of an application server. In addition, the definitions (i.e., information used for binding a particular role to an activity to be performed) that enable staff resolution using the current technologies are created at process development time. Since the human entities responsible for performing business activities are defined at development time, these definitions represent a very static aspect of such business processes. Any changes to the definitions will require rebuilding and redeploying the business process. The rebuilding of business processes are generally not feasible in a customer environment where only the binaries of these processes are available to the customer. Additionally, the customer may not want to invest in the skills which are necessary to implement these changes. Although there are sophisticated scenarios in which some flexibility is built into a business process by way of parameterizing role to business activity, the binding of business activities to roles and human entities still remains static in nature, in that no additional entities or roles in an organization may be further added to the business process without having to rebuild the process.
- The illustrative embodiments provide a computer implemented method, data processing system, and computer program product for dynamically binding business process activities to human entities at deployment time. Identification information about a staff activity in a business process is received from a process server at an access control system external to the process server. Responsive to initiation of the business process, the staff activity is resolved at the access control system at runtime by assigning the staff activity to a user based on an access policy of the access control system to form a staff activity assignment. The staff activity assignment is communicated from the access control system to the process server. The process in the illustrative embodiments allows the development of the business process to be entirely decoupled from staff activity resolution at runtime.
- The novel features believed characteristic of the invention are set forth in the appended claims. The invention itself, however, as well as a preferred mode of use, further objectives and advantages thereof, will best be understood by reference to the following detailed description of an illustrative embodiment when read in conjunction with the accompanying drawings, wherein:
-
FIG. 1 depicts a pictorial representation of a distributed data processing system in which the illustrative embodiments may be implemented; -
FIG. 2 is a block diagram of a data processing system in which the illustrative embodiments may be implemented; -
FIG. 3 is a block diagram of exemplary components for implementing the policy-based access control of business process activities in accordance with the illustrative embodiments; and -
FIG. 4 is a flowchart of a process for dynamically binding business process activities to human entities in accordance with the illustrative embodiments. - With reference now to the figures and in particular with reference to
FIGS. 1-2 , exemplary diagrams of data processing environments are provided in which illustrative embodiments may be implemented. It should be appreciated thatFIGS. 1-2 are only exemplary and are not intended to assert or imply any limitation with regard to the environments in which different embodiments may be implemented. Many modifications to the depicted environments may be made. -
FIG. 1 depicts a pictorial representation of a network of data processing systems in which illustrative embodiments may be implemented. Networkdata processing system 100 is a network of computers in which the illustrative embodiments may be implemented. Networkdata processing system 100 containsnetwork 102, which is the medium used to provide communications links between various devices and computers connected together within networkdata processing system 100. Network 102 may include connections, such as wire, wireless communication links, or fiber optic cables. - In the depicted example,
server 104 andserver 106 connect tonetwork 102 along withstorage unit 108. In addition,clients network 102.Clients server 104 provides data, such as boot files, operating system images, and applications toclients Clients data processing system 100 may include additional servers, clients, and other devices not shown. - In the depicted example, network
data processing system 100 is the Internet withnetwork 102 representing a worldwide collection of networks and gateways that use the Transmission Control Protocol/Internet Protocol (TCP/IP) suite of protocols to communicate with one another. At the heart of the Internet is a backbone of high-speed data communication lines between major nodes or host computers, consisting of thousands of commercial, governmental, educational and other computer systems that route data and messages. Of course, networkdata processing system 100 also may be implemented as a number of different types of networks, such as for example, an intranet, a local area network (LAN), or a wide area network (WAN).FIG. 1 is intended as an example, and not as an architectural limitation for the different illustrative embodiments. - With reference now to
FIG. 2 , a block diagram of a data processing system is shown in which illustrative embodiments may be implemented.Data processing system 200 is an example of a computer, such asserver 104 orclient 110 inFIG. 1 , in which computer usable program code or instructions implementing the processes may be located for the illustrative embodiments. - In the depicted example,
data processing system 200 employs a hub architecture including a north bridge and memory controller hub (NB/MCH) 202 and a south bridge and input/output (I/O) controller hub (SB/ICH) 204.Processing unit 206,main memory 208, andgraphics processor 210 are coupled to north bridge andmemory controller hub 202.Processing unit 206 may contain one or more processors and even may be implemented using one or more heterogeneous processor systems.Graphics processor 210 may be coupled to the NB/MCH through an accelerated graphics port (AGP), for example. - In the depicted example, local area network (LAN)
adapter 212 is coupled to south bridge and I/O controller hub 204 andaudio adapter 216, keyboard andmouse adapter 220,modem 222, read only memory (ROM) 224, universal serial bus (USB) andother ports 232, and PCI/PCIe devices 234 are coupled to south bridge and I/O controller hub 204 throughbus 238, and hard disk drive (HDD) 226 and CD-ROM 230 are coupled to south bridge and I/O controller hub 204 throughbus 240. PCI/PCIe devices may include, for example, Ethernet adapters, add-in cards, and PC cards for notebook computers. PCI uses a card bus controller, while PCIe does not.ROM 224 may be, for example, a flash binary input/output system (BIOS).Hard disk drive 226 and CD-ROM 230 may use, for example, an integrated drive electronics (IDE) or serial advanced technology attachment (SATA) interface. A super I/O (SIO)device 236 may be coupled to south bridge and I/O controller hub 204. - An operating system runs on
processing unit 206 and coordinates and provides control of various components withindata processing system 200 inFIG. 2 . The operating system may be a commercially available operating system such as Microsoft? Windows? XP (Microsoft and Windows are trademarks of Microsoft Corporation in the United States, other countries, or both). An object oriented programming system, such as the Java? programming system, may run in conjunction with the operating system and provides calls to the operating system from Java? programs or applications executing ondata processing system 200. Java? and all JavaT?-based trademarks are trademarks of Sun Microsystems, Inc. in the United States, other countries, or both. - Instructions for the operating system, the object-oriented programming system, and applications or programs are located on storage devices, such as
hard disk drive 226, and may be loaded intomain memory 208 for execution by processingunit 206. The processes of the illustrative embodiments may be performed by processingunit 206 using computer implemented instructions, which may be located in a memory such as, for example,main memory 208, read onlymemory 224, or in one or more peripheral devices. - The hardware in
FIGS. 1-2 may vary depending on the implementation. Other internal hardware or peripheral devices, such as flash memory, equivalent non-volatile memory, or optical disk drives and the like, may be used in addition to or in place of the hardware depicted inFIGS. 1-2 . Also, the processes of the illustrative embodiments may be applied to a multiprocessor data processing system. - In some illustrative examples,
data processing system 200 may be a personal digital assistant (PDA), which is generally configured with flash memory to provide non-volatile memory for storing operating system files and/or user-generated data. A bus system may be comprised of one or more buses, such as a system bus, an I/O bus and a PCI bus. Of course the bus system may be implemented using any type of communications fabric or architecture that provides for a transfer of data between different components or devices attached to the fabric or architecture. A communications unit may include one or more devices used to transmit and receive data, such as a modem or a network adapter. A memory may be, for example,main memory 208 or a cache such as found in north bridge andmemory controller hub 202. A processing unit may include one or more processors or CPUs. The depicted examples inFIGS. 1-2 and above-described examples are not meant to imply architectural limitations. For example,data processing system 200 also may be a tablet computer, laptop computer, or telephone device in addition to taking the form of a PDA. - As previously mentioned, certain computer processes are often termed “business processes”, as these business processes are computer processes which are often customized to a particular company's needs and typically involve some amount of human interaction. Since most organizations classify their personnel into different organizational roles based on the tasks performed by each individual, the actions of any particular individual may be restricted to those operations that are appropriate for the individual's role in the organization based on policy rules. The process of binding a task to an individual or organizational role (“staff resolution”) comprises deciding which user in the organization is allowed to perform the activity in a business process.
- The illustrative embodiments provide a dynamic method and system for binding a business process activity to a corresponding human entity or organizational role. In contrast with existing staff resolution techniques, such as those offered by Websphere Process Choreographer, which are provided by and supported by the process engine of the application server, the illustrative embodiments decouple the policy-based authorization from the process engine and externalize this authorization in a policy-based access control system. In addition, with the illustrative embodiments, binding is implemented at deployment time through the policy-based access control system. By externalizing the assignment of business process activities to organizational roles or human entities to the access control system, the dynamic process in the illustrative embodiments does not need to rely on definitions created at development time to implement the binding process, and thus the process avoids the static nature of existing staff resolution techniques. In addition, implementing the binding process at deployment time in the access control system shields a user from having to re-build and re-deploy a business process when a change occurs in the underlying definitions which enable staff resolution.
- The dynamic staff resolution process described in the illustrative embodiments provides several advantages over existing staff resolution techniques. For instance, with the illustrative embodiments, the binding of human entities to staff activities of a process is completely dynamic and is process-independent. Existing staff resolution techniques implement this binding as part of the process logic. Thus, a business process developer using the illustrative embodiments may focus solely on the business process logic at development time, rather than having to be concerned over binding of staff activities to human entities. In addition, human intervention during business process activities may be subject to various rules. For instance, a particular approval process may require the approval of an entire set of persons exercising a particular role or a subset thereof. Similarly, another policy may render the tasks to an automatic approval based on the satisfaction of pre-set conditions. Since the binding in the illustrative embodiments is delegated to an access control system, roles, users and deciding rules may be updated at deployment time to accommodate the needs of the organization. Furthermore, with the illustrative embodiments, the staff service component in products such as Websphere Process Choreographer becomes a very light-weight component of the process engine, as the staff service component simply acts as an interface to the underlying access control system.
-
FIG. 3 is a block diagram of exemplary components for implementing the policy-based access control of business process activities in accordance with the illustrative embodiments. In particular,FIG. 3 illustrates how the binding of human entities to business process activities is implemented within an access control system. -
Data processing system 300 in this illustrative example comprisesbusiness process engine 302,access control interface 304, andaccess control system 306.Business process engine 302 is a process server, which may be implemented asserver FIG. 1 .Business process engine 302 contains the runtime components necessary to execute a business process, and interprets the business processes defined by a business process developer in order to execute and manage business transactions.Business process engine 302 oversees the business transactions in the data processing system by reminding an individual or group participant of their assigned staff activities, such as via a calendar or email program.Business process engine 302 also may act as a client device to accesscontrol system 306. -
Access control interface 304 allowsbusiness process engine 302 to interface with external systems. In this illustrative example, a Java? Authorization Contract for Container (JACC) interface is used as theaccess control interface 304, although other appropriate interfaces may also be used. JACC provides the ability to delegate access decisions to an external provider, such asaccess control system 306.Business process engine 302 is interfaced via JACC to accesscontrol system 306. -
Access control system 306 is an authorization provider external tobusiness process engine 302 which receives information about a user security context and determines whether any activities are assigned to the user.Access control system 306 may be located on anyserver FIG. 1 .Access control system 306 protects resources (business process activities) in the system by making them available to users who are identified as assigned to those resources.Access control system 306 may include a user registry, such as a corporate LDAP server or a database, comprising user and group/role information. Resources may be defined and mapped to particular users and roles within the organization to constrain resource access based on these mappings. This mapping may be to one or more individual users by name, to one or more defined groups of users, or any combination of these. These mappings may be stored as role-based access control lists (ACLs) withinaccess control system 306. An example of an access control system is Tivoli? Access Manager, a product of International Business Machines Corporation. - The binding of staff activities and human entities or organizational roles in the illustrative embodiments occurs in a dynamic, rather than static, fashion. At
process development time 308, a process development tool outputs only identification information of thestaff activities 310 contained in a business process. For example, identification information of eachstaff activity 310 may be output in a tuple, such as: -
- <Process Name-Identifier, Activity Name-Identifier, Business Object>.
The process name identification and activity name identification may be obtained frombusiness process engine 302. The business object refers to the resource(s) that will be affected by the actions of the staff activity. Examples of resources which may be affected include, among others, both physical resources such as computer systems, machines, and equipment, and logical entities such as customer records, accounts, and orders.
- <Process Name-Identifier, Activity Name-Identifier, Business Object>.
-
Business process engine 302 then exports the identification information of astaff activity 310 in tuple form, and imported to an authorization policy engine inaccess control system 306. The authorization policy engine inaccess control system 306 comprises policy information required to determine the binding of each staff activity to a corresponding human entity or an organizational role, or to a rule based policy statement whenaccess control system 306 supports such rules. -
Access control system 306 then stores the tuple inaccess policy store 312. It should be noted that storing staff activity information withinaccess control system 306 is a departure from existing staff resolution mechanisms which persist this staff activity information in their own control structures, rather than in a control system external to accesscontrol system 306.Access policy store 312 also comprises role-based access control lists (ACLs), whichaccess control system 306 uses to form the bindings between the staff activities and the human entities or organizational roles based on the information in the tuple. - When a particular business process is instantiated, the business process runs until the process reaches a point in its workflow where a human intervention is required (i.e., reached a staff activity). When a user authenticates (logs on) to the system and checks if the user has a pending staff activity, the resolution of that staff activity to a human entity is performed by
access control system 306, communicated back tobusiness process engine 302, and provided to the requesting user. For instance, upon a user login,business process engine 302 may invokeaccess control system 306 by passing the user security context (e.g. an authenticated identity and its group/role information) toaccess control system 306.Access control system 306 queries the access control lists (ACLs) inaccess policy store 312 against the user information and returns <Process Name, Activity Name> of each activity that is awaiting the user's intervention.Business process engine 302 provides this user information to accesscontrol system 306 and allowsaccess control system 306 to make an access decision (i.e., a determination whether the user has any pending staff activities assigned).Access control system 306 provides the pending staff activity information tobusiness process engine 302, which in turn provides the activity information to the user. -
Access control system 306 may also determine whether or not access to a resource may be given to an entity by first determining whether the entity has access to the process activity template. For example, a change requester may instantiate a change management process only if the requester is allowed access to the underlying change management process template. A process template is a generic process definition that has not yet been customized to a particular environment, such as a change management process template in which staff activities have not yet been defined. -
FIG. 4 is a flowchart of a process for dynamically binding business process activities to human entities in accordance with the illustrative embodiments. The process described inFIG. 4 may be implemented in a data processing system, such asdata processing system 300 inFIG. 3 . The process begins at development time, where a process development tool used to define a process outputs information about all of the tool's staff activities (step 402). This information may comprise identification information about the staff activities in tuple form, which includes an identifier of a business process, an identifier of a particular staff activity in the process, and the business objects which will be affected by the actions of the staff activity. - The process server then exports the identification information containing information about the staff activity in tuple form to an authorization policy engine in an external access control system (step 404). The access control system comprises policy information required to determine the binding of each business activity to a corresponding human entity or an organizational role. The external access control system then imports and stores the identification information in an access policy store within the access control system (step 406).
- When a business process is initiated, the business process instructs the external access control system to resolve the staff activities in the business process which have no dependency on other staff activities (step 408). In this instance, resolution means assigning staff activities to the entitled human entities based on the access policy of the access control system. The resolved staff activities are communicated back from the access control system to the process server (step 410).
- When a user authenticates (logs on) to the process server and checks if the user has a pending staff activity, the process server provides the user with those staff activities which were assigned to the user by the access control system based on the access policy (step 412). For example, the process server may provide the business process name and the business activity name to the user which are pending the user's intervention. The user may then perform the business activities dynamically assigned to the user by the access control system (step 414).
- A determination is then made as to whether there are any other staff activities in the business process which should be resolved (step 416). If there are more staff activities to be resolved (‘yes’ output of step 416), the process loops back to
step 408. If there are no more staff activities to be resolved (‘no’ output of step 416), the process terminates thereafter. - The invention can take the form of an entirely hardware embodiment, an entirely software embodiment or an embodiment containing both hardware and software elements. In a preferred embodiment, the invention is implemented in software, which includes but is not limited to firmware, resident software, microcode, etc.
- Furthermore, the invention can take the form of a computer program product accessible from a computer-usable or computer-readable medium providing program code for use by or in connection with a computer or any instruction execution system. For the purposes of this description, a computer-usable or computer readable medium can be any tangible apparatus that can contain, store, communicate, propagate, or transport the program for use by or in connection with the instruction execution system, apparatus, or device.
- The medium can be an electronic, magnetic, optical, electromagnetic, infrared, or semiconductor system (or apparatus or device) or a propagation medium. Examples of a computer-readable medium include a semiconductor or solid state memory, magnetic tape, a removable computer diskette, a random access memory (RAM), a read-only memory (ROM), a rigid magnetic disk and an optical disk. Current examples of optical disks include compact disk—read only memory (CD-ROM), compact disk—read/write (CD-R/W) and DVD.
- A data processing system suitable for storing and/or executing program code will include at least one processor coupled directly or indirectly to memory elements through a system bus. The memory elements can include local memory employed during actual execution of the program code, bulk storage, and cache memories which provide temporary storage of at least some program code in order to reduce the number of times code must be retrieved from bulk storage during execution.
- Input/output or I/O devices (including but not limited to keyboards, displays, pointing devices, etc.) can be coupled to the system either directly or through intervening I/O controllers.
- Network adapters may also be coupled to the system to enable the data processing system to become coupled to other data processing systems or remote printers or storage devices through intervening private or public networks. Modems, cable modem and Ethernet cards are just a few of the currently available types of network adapters.
- The description of the present invention has been presented for purposes of illustration and description, and is not intended to be exhaustive or limited to the invention in the form disclosed. Many modifications and variations will be apparent to those of ordinary skill in the art. The embodiment was chosen and described in order to best explain the principles of the invention, the practical application, and to enable others of ordinary skill in the art to understand the invention for various embodiments with various modifications as are suited to the particular use contemplated.
Claims (20)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US11/738,794 US8904391B2 (en) | 2025-08-05 | 2025-08-05 | Policy-based access control approach to staff activities of a business process |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US11/738,794 US8904391B2 (en) | 2025-08-05 | 2025-08-05 | Policy-based access control approach to staff activities of a business process |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| US20080263060A1 true US20080263060A1 (en) | 2025-08-05 |
| US8904391B2 US8904391B2 (en) | 2025-08-05 |
Family
ID=39873282
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US11/738,794 Expired - Fee Related US8904391B2 (en) | 2025-08-05 | 2025-08-05 | Policy-based access control approach to staff activities of a business process |
Country Status (1)
| Country | Link |
|---|---|
| US (1) | US8904391B2 (en) |
Cited By (8)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20110302290A1 (en) * | 2025-08-05 | 2025-08-05 | Novell, Inc. | System and method for managing changes in a network datacenter |
| FR2964770A1 (en) * | 2025-08-05 | 2025-08-05 | Evidian | Method for processing e.g. permission or roll demand, made by person of enterprise in workflow engine of information system to allow person to have access to color printer, involves sending response to engine via authorization system |
| US20130346134A1 (en) * | 2025-08-05 | 2025-08-05 | Siemens Enterprise Communications Gmbh & Co. Kg | System and method for coordinating and controlling production processes and inter-related decision making process |
| US20140129268A1 (en) * | 2025-08-05 | 2025-08-05 | Oracle International Corporation | Role discovery using privilege cluster analysis |
| US20140164052A1 (en) * | 2025-08-05 | 2025-08-05 | Hartford Fire Insurance Company | System and Method for Managing and Displaying Company Policy Data |
| US20150051957A1 (en) * | 2025-08-05 | 2025-08-05 | Oracle International Corporation | Measuring customer experience value |
| US9760734B2 (en) * | 2025-08-05 | 2025-08-05 | Sap Se | Catalog-based user authorization to access to multiple applications |
| US20180067979A1 (en) * | 2025-08-05 | 2025-08-05 | Salesforce.Com, Inc. | System, method and computer program product for maintaining data stored in a data structure |
Citations (62)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5369702A (en) * | 2025-08-05 | 2025-08-05 | Tecsec Incorporated | Distributed cryptographic object method |
| US5764958A (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Method and apparatus for creating dynamic roles with a system object model |
| US5911143A (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Method and system for advanced role-based access control in distributed and centralized computer systems |
| US5974420A (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Information exchange operator for a tuplespace |
| US6088679A (en) * | 2025-08-05 | 2025-08-05 | The United States Of America As Represented By The Secretary Of Commerce | Workflow management employing role-based access control |
| US6141720A (en) * | 2025-08-05 | 2025-08-05 | Cabletron Systems, Inc. | Method and apparatus for coordination of a shared object in a distributed system |
| US6202066B1 (en) * | 2025-08-05 | 2025-08-05 | The United States Of America As Represented By The Secretary Of Commerce | Implementation of role/group permission association using object access type |
| US20010001864A1 (en) * | 2025-08-05 | 2025-08-05 | Page John D. | Trackpoint-based computer-implemented systems and methods for facilitating collaborative project development and communication |
| US20010047485A1 (en) * | 2025-08-05 | 2025-08-05 | Daniel Brown | Computer security system |
| US20020147801A1 (en) * | 2025-08-05 | 2025-08-05 | Gullotta Tony J. | System and method for provisioning resources to users based on policies, roles, organizational information, and attributes |
| US20020178119A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Method and system for a role-based access control model with active roles |
| US20030018519A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Computerized method and system for maturity assessment of business processes |
| US6529909B1 (en) * | 2025-08-05 | 2025-08-05 | Accenture Llp | Method for translating an object attribute converter in an information services patterns environment |
| US20030046576A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Role-permission model for security policy administration and enforcement |
| US20030084168A1 (en) * | 2025-08-05 | 2025-08-05 | Erickson John S. | Policy enforcement and access control for distributed networked services |
| US20030112666A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Security and authorization development tools |
| US6751619B1 (en) * | 2025-08-05 | 2025-08-05 | Microsoft Corporation | Methods and apparatus for tuple management in data processing system |
| US20040128186A1 (en) * | 2025-08-05 | 2025-08-05 | Jodi Breslin | System and method for managing risks associated with outside service providers |
| US20040205342A1 (en) * | 2025-08-05 | 2025-08-05 | Roegner Michael W. | Method and system for dynamically implementing an enterprise resource policy |
| US20050038006A1 (en) * | 2025-08-05 | 2025-08-05 | Shangold Gary A. | Triphasic oral contraceptive |
| US20050044227A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Reservation of TCP/UDP ports using UID, GID or process name |
| US20050132048A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Role-based views access to a workflow weblog |
| US20050138031A1 (en) * | 2025-08-05 | 2025-08-05 | Wefers Wolfgang M. | Systems and methods for assigning task-oriented roles to users |
| US20050165809A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Technique for improving staff queries in a workflow management system |
| US20050182773A1 (en) * | 2025-08-05 | 2025-08-05 | Feinsmith Jason B. | Machine-implemented activity management system using asynchronously shared activity data objects and journal data items |
| US20050203757A1 (en) * | 2025-08-05 | 2025-08-05 | Hui Lei | System and method for pervasive enablement of business processes |
| US20050267765A1 (en) * | 2025-08-05 | 2025-08-05 | Jun-Jang Jeng | Apparatus and method for policy-driven business process exception handling |
| US20060005124A1 (en) * | 2025-08-05 | 2025-08-05 | Ewald Speicher | User interface for complex process implementation |
| US20060004783A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Dynamic binding of principal services in a cross-enterprise business process management system |
| US20060009991A1 (en) * | 2025-08-05 | 2025-08-05 | Jun-Jang Jeng | Method and apparatus for using meta-rules to support dynamic rule-based business systems |
| US6988139B1 (en) * | 2025-08-05 | 2025-08-05 | Microsoft Corporation | Distributed computing of a job corresponding to a plurality of predefined tasks |
| US20060036869A1 (en) * | 2025-08-05 | 2025-08-05 | Bill Faught | Methods and systems that provide user access to computer resources with controlled user access rights |
| US20060047558A1 (en) * | 2025-08-05 | 2025-08-05 | Norimasa Uchiyama | Method, system, and computer program product for assigning personnel to project tasks |
| US20060089938A1 (en) * | 2025-08-05 | 2025-08-05 | Leonard Glenda A | Distributed scalable policy based content management |
| US20060101019A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Systems and methods of access control enabling ownership of access control lists to users or groups |
| US20060106825A1 (en) * | 2025-08-05 | 2025-08-05 | Matthew Cozzi | Enterprise architecture analysis framework database |
| US20060111931A1 (en) * | 2025-08-05 | 2025-08-05 | General Electric Company | Method for the use of and interaction with business system transfer functions |
| US20060247965A1 (en) * | 2025-08-05 | 2025-08-05 | Griffith Wm P | Method of defining and monitoring processes |
| US20060268712A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | System, method, and service for dynamically selecting an optimum message pathway |
| US20070033571A1 (en) * | 2025-08-05 | 2025-08-05 | Sap Ag | Dynamic work center |
| US7185192B1 (en) * | 2025-08-05 | 2025-08-05 | Emc Corporation | Methods and apparatus for controlling access to a resource |
| US20070211056A1 (en) * | 2025-08-05 | 2025-08-05 | Sudip Chakraborty | Multi-dimensional data visualization |
| US20070239859A1 (en) * | 2025-08-05 | 2025-08-05 | Wilkinson Anthony J | Method and system for providing virtualized application workspaces |
| US20070239998A1 (en) * | 2025-08-05 | 2025-08-05 | Medox Exchange, Inc. | Dynamic binding of access and usage rights to computer-based resources |
| US7289964B1 (en) * | 2025-08-05 | 2025-08-05 | Accenture Llp | System and method for transaction services patterns in a netcentric environment |
| US20070271381A1 (en) * | 2025-08-05 | 2025-08-05 | Joseph Skeffington Wholey | Managing computing resources in graph-based computations |
| US20070283351A1 (en) * | 2025-08-05 | 2025-08-05 | Degenaro Louis R | Unified job processing of interdependent heterogeneous tasks |
| US20070299795A1 (en) * | 2025-08-05 | 2025-08-05 | Microsoft Corporation | Creating and managing activity-centric workflow |
| US20070300224A1 (en) * | 2025-08-05 | 2025-08-05 | Vijay Kumar Aggarwal | Method and apparatus to modify a task within a set of tasks |
| US20080022370A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Corporation | System and method for role based access control in a content management system |
| US7340513B2 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Resource management method and system with rule based consistency check |
| US7373310B1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Workflow system matrix organization search engine |
| US20080222602A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Declarative object identity using relation types |
| US20080256610A1 (en) * | 2025-08-05 | 2025-08-05 | Bea Systems, Inc. | System and method for dynamic role association |
| US20080294599A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Apparatus and method of semantic tuplespace system |
| US7469409B2 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Adaptive resource management method |
| US7523486B1 (en) * | 2025-08-05 | 2025-08-05 | Sprint Communications Company Lp | User administration tool |
| US20090213860A1 (en) * | 2025-08-05 | 2025-08-05 | Huawei Technologies Co., Ltd. | Method and device for service binding |
| US7610575B2 (en) * | 2025-08-05 | 2025-08-05 | Consona Crm Inc. | System and method for the composition, generation, integration and execution of business processes over a network |
| US7676831B2 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Role-based access control management for multiple heterogeneous application components |
| US7793333B2 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Mobile authorization using policy based access control |
| US8024275B2 (en) * | 2025-08-05 | 2025-08-05 | Sap Ag | Method and system for monitoring a business process |
Family Cites Families (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2004109443A2 (en) | 2025-08-05 | 2025-08-05 | Liquid Machines, Inc. | Managing data objects in dynamic, distributed and collaborative contexts |
-
2007
- 2025-08-05 US US11/738,794 patent/US8904391B2/en not_active Expired - Fee Related
Patent Citations (71)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US5369702A (en) * | 2025-08-05 | 2025-08-05 | Tecsec Incorporated | Distributed cryptographic object method |
| US5911143A (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Method and system for advanced role-based access control in distributed and centralized computer systems |
| US5764958A (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Method and apparatus for creating dynamic roles with a system object model |
| US6510478B1 (en) * | 2025-08-05 | 2025-08-05 | Aprisma Management Technologies Inc. | Method and apparatus for coordination of a shared object in a distributed system |
| US6141720A (en) * | 2025-08-05 | 2025-08-05 | Cabletron Systems, Inc. | Method and apparatus for coordination of a shared object in a distributed system |
| US20010001864A1 (en) * | 2025-08-05 | 2025-08-05 | Page John D. | Trackpoint-based computer-implemented systems and methods for facilitating collaborative project development and communication |
| US6202066B1 (en) * | 2025-08-05 | 2025-08-05 | The United States Of America As Represented By The Secretary Of Commerce | Implementation of role/group permission association using object access type |
| US6088679A (en) * | 2025-08-05 | 2025-08-05 | The United States Of America As Represented By The Secretary Of Commerce | Workflow management employing role-based access control |
| US5974420A (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Information exchange operator for a tuplespace |
| US20050038006A1 (en) * | 2025-08-05 | 2025-08-05 | Shangold Gary A. | Triphasic oral contraceptive |
| US6529909B1 (en) * | 2025-08-05 | 2025-08-05 | Accenture Llp | Method for translating an object attribute converter in an information services patterns environment |
| US7289964B1 (en) * | 2025-08-05 | 2025-08-05 | Accenture Llp | System and method for transaction services patterns in a netcentric environment |
| US20010047485A1 (en) * | 2025-08-05 | 2025-08-05 | Daniel Brown | Computer security system |
| US6751619B1 (en) * | 2025-08-05 | 2025-08-05 | Microsoft Corporation | Methods and apparatus for tuple management in data processing system |
| US7373310B1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Workflow system matrix organization search engine |
| US20080222147A1 (en) * | 2025-08-05 | 2025-08-05 | Alexandre El Homsi | Workflow system matrix organization search engine |
| US7185192B1 (en) * | 2025-08-05 | 2025-08-05 | Emc Corporation | Methods and apparatus for controlling access to a resource |
| US20020147801A1 (en) * | 2025-08-05 | 2025-08-05 | Gullotta Tony J. | System and method for provisioning resources to users based on policies, roles, organizational information, and attributes |
| US20020178119A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Method and system for a role-based access control model with active roles |
| US20080256610A1 (en) * | 2025-08-05 | 2025-08-05 | Bea Systems, Inc. | System and method for dynamic role association |
| US7823189B2 (en) * | 2025-08-05 | 2025-08-05 | Bea Systems, Inc. | System and method for dynamic role association |
| US20030018519A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Computerized method and system for maturity assessment of business processes |
| US20030046576A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Role-permission model for security policy administration and enforcement |
| US20030084168A1 (en) * | 2025-08-05 | 2025-08-05 | Erickson John S. | Policy enforcement and access control for distributed networked services |
| US20030112666A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Security and authorization development tools |
| US6988139B1 (en) * | 2025-08-05 | 2025-08-05 | Microsoft Corporation | Distributed computing of a job corresponding to a plurality of predefined tasks |
| US7340513B2 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Resource management method and system with rule based consistency check |
| US7469409B2 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Adaptive resource management method |
| US20040128186A1 (en) * | 2025-08-05 | 2025-08-05 | Jodi Breslin | System and method for managing risks associated with outside service providers |
| US7610575B2 (en) * | 2025-08-05 | 2025-08-05 | Consona Crm Inc. | System and method for the composition, generation, integration and execution of business processes over a network |
| US20040205342A1 (en) * | 2025-08-05 | 2025-08-05 | Roegner Michael W. | Method and system for dynamically implementing an enterprise resource policy |
| US20060111931A1 (en) * | 2025-08-05 | 2025-08-05 | General Electric Company | Method for the use of and interaction with business system transfer functions |
| US20050044227A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Reservation of TCP/UDP ports using UID, GID or process name |
| US20050149375A1 (en) * | 2025-08-05 | 2025-08-05 | Wefers Wolfgang M. | Systems and methods for handling and managing workflows |
| US20050138031A1 (en) * | 2025-08-05 | 2025-08-05 | Wefers Wolfgang M. | Systems and methods for assigning task-oriented roles to users |
| US20050132048A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Role-based views access to a workflow weblog |
| US20050165809A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Technique for improving staff queries in a workflow management system |
| US7197502B2 (en) * | 2025-08-05 | 2025-08-05 | Friendly Polynomials, Inc. | Machine-implemented activity management system using asynchronously shared activity data objects and journal data items |
| US20070150496A1 (en) * | 2025-08-05 | 2025-08-05 | Feinsmith Jason B | Machine-implemented activity management system using asynchronously shared activity data objects and journal data items |
| US20050182773A1 (en) * | 2025-08-05 | 2025-08-05 | Feinsmith Jason B. | Machine-implemented activity management system using asynchronously shared activity data objects and journal data items |
| US7523486B1 (en) * | 2025-08-05 | 2025-08-05 | Sprint Communications Company Lp | User administration tool |
| US20050203757A1 (en) * | 2025-08-05 | 2025-08-05 | Hui Lei | System and method for pervasive enablement of business processes |
| US20060004783A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Dynamic binding of principal services in a cross-enterprise business process management system |
| US20060009991A1 (en) * | 2025-08-05 | 2025-08-05 | Jun-Jang Jeng | Method and apparatus for using meta-rules to support dynamic rule-based business systems |
| US20050267765A1 (en) * | 2025-08-05 | 2025-08-05 | Jun-Jang Jeng | Apparatus and method for policy-driven business process exception handling |
| US20060005124A1 (en) * | 2025-08-05 | 2025-08-05 | Ewald Speicher | User interface for complex process implementation |
| US20060036869A1 (en) * | 2025-08-05 | 2025-08-05 | Bill Faught | Methods and systems that provide user access to computer resources with controlled user access rights |
| US20060047558A1 (en) * | 2025-08-05 | 2025-08-05 | Norimasa Uchiyama | Method, system, and computer program product for assigning personnel to project tasks |
| US20060089938A1 (en) * | 2025-08-05 | 2025-08-05 | Leonard Glenda A | Distributed scalable policy based content management |
| US20060101019A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Systems and methods of access control enabling ownership of access control lists to users or groups |
| US20060106825A1 (en) * | 2025-08-05 | 2025-08-05 | Matthew Cozzi | Enterprise architecture analysis framework database |
| US7970729B2 (en) * | 2025-08-05 | 2025-08-05 | Sap Aktiengesellschaft | Enterprise architecture analysis framework database |
| US20060247965A1 (en) * | 2025-08-05 | 2025-08-05 | Griffith Wm P | Method of defining and monitoring processes |
| US20060268712A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | System, method, and service for dynamically selecting an optimum message pathway |
| US7793333B2 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Mobile authorization using policy based access control |
| US20070033571A1 (en) * | 2025-08-05 | 2025-08-05 | Sap Ag | Dynamic work center |
| US7676831B2 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Role-based access control management for multiple heterogeneous application components |
| US7779091B2 (en) * | 2025-08-05 | 2025-08-05 | Vmware, Inc. | Method and system for providing virtualized application workspaces |
| US20080034071A1 (en) * | 2025-08-05 | 2025-08-05 | Wilkinson Anthony J | Method and system for providing virtualized application workspaces |
| US20070239859A1 (en) * | 2025-08-05 | 2025-08-05 | Wilkinson Anthony J | Method and system for providing virtualized application workspaces |
| US20070211056A1 (en) * | 2025-08-05 | 2025-08-05 | Sudip Chakraborty | Multi-dimensional data visualization |
| US20070239998A1 (en) * | 2025-08-05 | 2025-08-05 | Medox Exchange, Inc. | Dynamic binding of access and usage rights to computer-based resources |
| US20070271381A1 (en) * | 2025-08-05 | 2025-08-05 | Joseph Skeffington Wholey | Managing computing resources in graph-based computations |
| US20070283351A1 (en) * | 2025-08-05 | 2025-08-05 | Degenaro Louis R | Unified job processing of interdependent heterogeneous tasks |
| US20070300224A1 (en) * | 2025-08-05 | 2025-08-05 | Vijay Kumar Aggarwal | Method and apparatus to modify a task within a set of tasks |
| US20070299795A1 (en) * | 2025-08-05 | 2025-08-05 | Microsoft Corporation | Creating and managing activity-centric workflow |
| US20080022370A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Corporation | System and method for role based access control in a content management system |
| US20090213860A1 (en) * | 2025-08-05 | 2025-08-05 | Huawei Technologies Co., Ltd. | Method and device for service binding |
| US20080222602A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Declarative object identity using relation types |
| US8024275B2 (en) * | 2025-08-05 | 2025-08-05 | Sap Ag | Method and system for monitoring a business process |
| US20080294599A1 (en) * | 2025-08-05 | 2025-08-05 | International Business Machines Corporation | Apparatus and method of semantic tuplespace system |
Cited By (16)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20180067979A1 (en) * | 2025-08-05 | 2025-08-05 | Salesforce.Com, Inc. | System, method and computer program product for maintaining data stored in a data structure |
| US11609896B2 (en) * | 2025-08-05 | 2025-08-05 | Salesforce.Com, Inc. | System, method and computer program product for maintaining data stored in a data structure |
| US20220107934A1 (en) * | 2025-08-05 | 2025-08-05 | Salesforce.Com, Inc. | System, method and computer program product for maintaining data stored in a data structure |
| US11120003B2 (en) * | 2025-08-05 | 2025-08-05 | Salesforce.Com, Inc. | System, method and computer program product for maintaining data stored in a data structure |
| US8745188B2 (en) * | 2025-08-05 | 2025-08-05 | Novell, Inc. | System and method for managing changes in a network datacenter |
| US8769084B2 (en) | 2025-08-05 | 2025-08-05 | Novell, Inc. | System and method for modeling interdependencies in a network datacenter |
| US9432277B2 (en) | 2025-08-05 | 2025-08-05 | Novell, Inc. | System and method for modeling interdependencies in a network datacenter |
| US20110302290A1 (en) * | 2025-08-05 | 2025-08-05 | Novell, Inc. | System and method for managing changes in a network datacenter |
| FR2964770A1 (en) * | 2025-08-05 | 2025-08-05 | Evidian | Method for processing e.g. permission or roll demand, made by person of enterprise in workflow engine of information system to allow person to have access to color printer, involves sending response to engine via authorization system |
| US20170337501A1 (en) * | 2025-08-05 | 2025-08-05 | Unify Gmbh & Co. Kg | System and method for coordinating and controlling production processes and inter-related decision making processes |
| US20130346134A1 (en) * | 2025-08-05 | 2025-08-05 | Siemens Enterprise Communications Gmbh & Co. Kg | System and method for coordinating and controlling production processes and inter-related decision making process |
| US9679264B2 (en) * | 2025-08-05 | 2025-08-05 | Oracle International Corporation | Role discovery using privilege cluster analysis |
| US20140129268A1 (en) * | 2025-08-05 | 2025-08-05 | Oracle International Corporation | Role discovery using privilege cluster analysis |
| US20140164052A1 (en) * | 2025-08-05 | 2025-08-05 | Hartford Fire Insurance Company | System and Method for Managing and Displaying Company Policy Data |
| US20150051957A1 (en) * | 2025-08-05 | 2025-08-05 | Oracle International Corporation | Measuring customer experience value |
| US9760734B2 (en) * | 2025-08-05 | 2025-08-05 | Sap Se | Catalog-based user authorization to access to multiple applications |
Also Published As
| Publication number | Publication date |
|---|---|
| US8904391B2 (en) | 2025-08-05 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US8904391B2 (en) | Policy-based access control approach to staff activities of a business process | |
| Thakare et al. | PARBAC: Priority-attribute-based RBAC model for azure IoT cloud | |
| US8136146B2 (en) | Secure audit log access for federation compliance | |
| US8707383B2 (en) | Computer workload management with security policy enforcement | |
| US8732290B2 (en) | Virtual workplace software based on organization characteristics | |
| US9152401B2 (en) | Methods and systems for generating and delivering an interactive application delivery store | |
| US10679141B2 (en) | Using classification data as training set for auto-classification of admin rights | |
| US20110162034A1 (en) | Discovery and management of context-based entitlements across loosely-coupled environments | |
| US9077704B2 (en) | Multiple authentication support in a shared environment | |
| US8019845B2 (en) | Service delivery using profile based management | |
| US20080082761A1 (en) | Generic locking service for business integration | |
| EP1967993A1 (en) | Dynamic workflow resource authentication and discovery | |
| US20080306806A1 (en) | Methods and apparatus for dynamically allocating tasks | |
| US8522307B2 (en) | Flexibly assigning security configurations to applications | |
| US9600666B1 (en) | Dynamic optimizing scanner for identity and access management (IAM) compliance verification | |
| US20090063494A1 (en) | Method and system to synchronize account names across a plurality of security systems | |
| US20090006618A1 (en) | Methods and systems for access routing and resource mapping using filters | |
| US12132737B2 (en) | Systems and methods for automated cloud provisioning | |
| US8819231B2 (en) | Domain based management of partitions and resource groups | |
| CA2717505A1 (en) | Method and apparatus for dynamic provisioning in data processing environment | |
| US20230135054A1 (en) | System and Methods for Agentless Managed Device Identification as Part of Setting a Security Policy for a Device | |
| US20130311221A1 (en) | Evaluating deployment readiness in delivery centers through collaborative requirements gathering | |
| US20050071667A1 (en) | Heterogenous domain-based routing mechanism for user authentication | |
| US10243994B2 (en) | Quantitatively measuring recertification campaign effectiveness | |
| KR20060128598A (en) | Method and system for membership determination through script |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment |
Owner name: INTERNATIONAL BUSINESS MACHINES CORPORATION, NEW Y Free format text: ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:BENANTAR, MESSAOUD B;MADDURI, HARI HARANATH;SIGNING DATES FROM 20070330 TO 20070419;REEL/FRAME:019195/0075 Owner name: INTERNATIONAL BUSINESS MACHINES CORPORATION, NEW Y Free format text: ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:BENANTAR, MESSAOUD B;MADDURI, HARI HARANATH;REEL/FRAME:019195/0075;SIGNING DATES FROM 20070330 TO 20070419 |
|
| FEPP | Fee payment procedure |
Free format text: MAINTENANCE FEE REMINDER MAILED (ORIGINAL EVENT CODE: REM.) |
|
| LAPS | Lapse for failure to pay maintenance fees |
Free format text: PATENT EXPIRED FOR FAILURE TO PAY MAINTENANCE FEES (ORIGINAL EVENT CODE: EXP.); ENTITY STATUS OF PATENT OWNER: LARGE ENTITY |
|
| STCH | Information on status: patent discontinuation |
Free format text: PATENT EXPIRED DUE TO NONPAYMENT OF MAINTENANCE FEES UNDER 37 CFR 1.362 |
|
| FP | Lapsed due to failure to pay maintenance fee |
Effective date: 20181202 |